Home
Recommended
Other Links
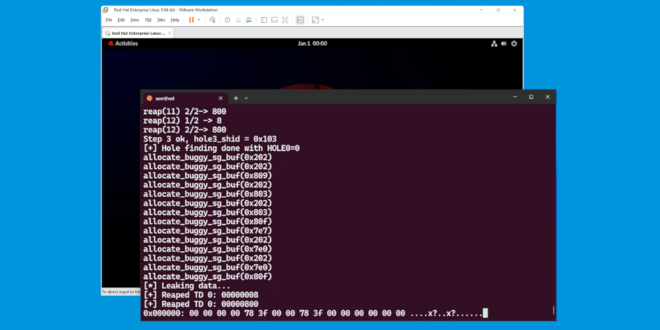
On the clock: Escaping VMware Workstation at Pwn2Own Berlin 2025
North Korea-linked threat group KONNI targets countries across APAC, specifically in blockchain sectors, with AI-generated malware
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Well, well, well - look what we’re back with.
You may recall that merely two weeks ago, we analyzed CVE-2025-52691 - a pre-auth RCE vulnerability in the SmarterTools SmarterMail email solution with a timeline that is typically reserved for KEV holders.
The plot of that story had everything;
* A government agency
* Vague patch notes (in our opinion)
* Fairly tense forum posts
* Accusations of in-the-wild exploitation
The sort of thing dreams are made of~
Why Are We Here?
Well, as alway
### Summary
It is still possible (albeit with significantly more effort) to upload a specially crafted Wheel file (i.e. zip) to PyPI that when installed with PIP (or another Python zipfile based t...
# Intercepting OkHttp at Runtime With Frida - A Practical Guide
22 Jan 2026 - Posted by Szymon Drosdzol
### Introduction
OkHttp is the defacto standard HTTP client library for the Android ecosystem. It is therefore crucial for a security analyst to be able to dynamically eavesdrop the traffic...
Learn how we are using the newly released GitHub Security Lab Taskflow Agent to triage categories of vulnerabilities in GitHub Actions and JavaScript projects.
VoidLink's framework marks the first evidence of fully AI-designed and built advanced malware, beginning a new era of AI-generated malware
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Windows has supported computer telephony integration for decades, providing applications with the ability to manage phone devices, lines, and calls. While modern deployments increasingly rely on cloud-based telephony solutions, classic telephony services remain available out of the box in Windows and continue to be used in specialized environments. As a result, legacy telephony components still […]
Recently I ran an experiment where I built agents on top of Opus 4.5 and GPT-5.2 and then challenged them to write exploits for a zeroday vulnerability in the QuickJS Javascript interpreter. I adde…
Consuming from Microsoft-Windows-Threat-Intelligence without Antimalware-PPL or kernel patching/driver loading.
"In this post, we\u0026rsquo;ll look how an adversary can mint authentication cookies for Next.js (next-auth/Auth.js) applications to maintain persistent access to …"
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Announcing GitHub Security Lab Taskflow Agent, an open source and collaborative framework for security research with AI.
Key findings Introduction In December 2025, a previously unknown Ransomware-as-a-Service (RaaS) operation calling itself Sicarii began advertising its services across multiple underground platforms. The group’s name references the Sicarii, a 1st-century Jewish assassins group that opposed Roman rule in Judea. From its initial appearance, the Sicarii ransomware group distinguished itself through unusually explicit and persistent use of Israeli […]
Mobile app security has become significantly harder over the past few years. Modern mobile applications rely on dozens of third-party SDKs, complex authentication flows, background services, deeplinks, and constant interaction with device-level APIs.
Wireless-(in)Fidelity: Pentesting Wi-Fi in 2025
The new framework maintains long-term access to Linux systems while operating reliably in cloud and container environments
Welcome to 2026!
While we are all waiting for the scheduled SSLVPN ITW exploitation programming that occurs every January, we’re back from Christmas and idle hands, idle minds, yada yada.
In December, we were alerted to a vulnerability in SmarterTools’ SmarterMail solution, accompanied by an advisory from Singapore’s Cyber Security Agency (CSA) - CVE-2025-52691, a pre-auth RCE that obtained full marks (10/10) on the industry’s scale.
Vulnerabilities like these are always exciting, because whe
Eight years ago today, I started STAR Labs by hiring several fresh grads with no working experiences.
Today, I stand here with a different group of faces. Some of you were there from the beginning. Some of you joined along the way. Some of you just started last month.
And some of the people who were here… weren’t anymore.
Not because they failed. Not because we failed them. But because life called them in different directions.
Key takeaways Introduction GoBruteforcer is a botnet that turns compromised Linux servers into scanning and password brute-force nodes. It targets internet-exposed services such as phpMyAdmin web panels, MySQL and PostgreSQL databases, and FTP servers. Infected hosts are incorporated into the botnet and accept remote operator commands. Newly discovered weak credentials are used to steal data, […]
Disclaimer: This article is intended for educational purposes and security specialists conducting authorized testing. The author assumes no responsibility for any misuse of the information provided. Distribution of malicious software, system disruption, and privacy violations are punishable by law.
Introduction I’m sure most of you are already familiar with the concept of Prompt Injection and its various consequences. However, in 2026, any AI model without MCP (Model Context Protocol) servers can’t reach its full potential — that’s why developers are connecting numerous MCP servers to extend their capabilities.
Over the last year, security researchers have shared a huge amount of work with the community through blog posts, presentations, and whitepapers. This is great, but it also means genuinely reusable te
### Summary
A buffer overflow and stack information leak affecting the ARM Ampere Management Mode (MM) Boot Error Record Table (BERT) driver. This code is bundled into the ARM Unified Extensible F...
#### Summary
Multiple arbitrary Out-of-Bounds (OOB) `'\0'` byte write vulnerabilities affecting the ARM Ampere Management Mode (MM) PCIe driver were discovered. This code is bundled into t...
Interrupt discovery and delivery on Windows on ARM
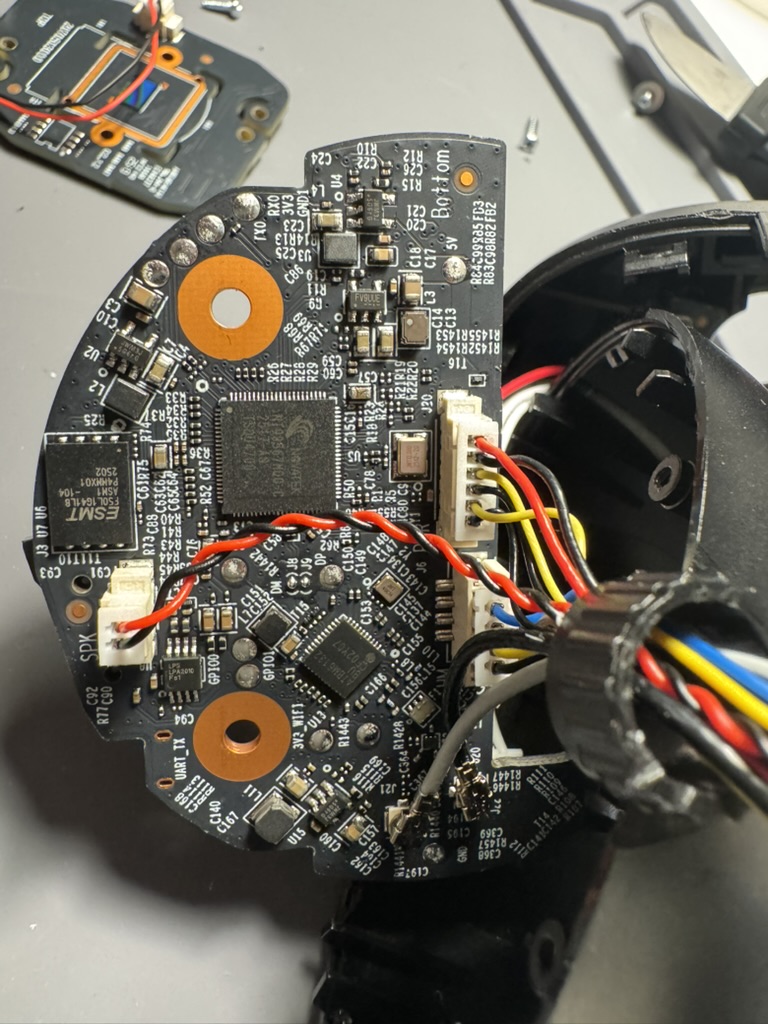
The Tapo C260 is the latest TP-Link camera featuring a whole host of upgrades. As part of the SPIRITCYBER contest where I found several RCEs and other interesting vulnerabilities, I decided to focus on this device and dive deeper into hardware hacking.
39C3 Talk: Agentic ProbLLMs - Exploiting AI Computer-Use And Coding Agents
Learn why some long-enrolled OSS-Fuzz projects still contain vulnerabilities and how you can find them.
Every day, thousands of web services generate PDF (Portable Document Format) files—bills, contracts, reports. This step is often treated as a technical routine, “just convert the HTML,” but in practice it’s exactly where a trust boundary is crossed. The renderer parses HTML, downloads external resources, processes fonts, SVGs, and images, and sometimes has access to […]
Most will talk about the success in their year-end posts. Great. Nobody talks about the failures. Nobody talks about what ACTUALLY happened.
Well, we are going to tell you about OUR STORY - the success AND the failures. The whole thing. Because that’s how we actually learn…from our own mistakes.
So here it is, UNFILTERED. Buckle up.
PWN2OWN 2025 BERLIN & IRELAND We could only bring one of our interns, Gerrard Tai, along with us to Pwn2Own.
Security advice for users and maintainers to help reduce the impact of the next supply chain malware attack.
The List-Unsubscribe SMTP header is standardized but often overlooked during security assessments. It allows email clients to provide an easy way for end-users to unsubscribe from mailing lists.
This post discusses how this header can be abused to perform Cross-Site Scripting (XSS) and Server-Side Request Forgery (SSRF) attacks in certain scenarios. Real-world examples involving Horde Webmail (CVE-2025-68673) and Nextcloud Mail App are provided to illustrate the risks.
Livewire: remote command execution through unmarshaling
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
### Impact Vendor
Palo Alto Networks
### Affected Product
PA-54xx All supported versions of PAN-OS.
Tested: PAN-OS 10.x - 10.2.16-h1 PAN-OS 11x - 11.2.1
### Important Dates
The report wa...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Check Point Research exposes GachiLoader, a Node.js loader in the YouTube Ghost Network, and shows how API tracing defeats its obfuscation.
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Key Findings Introduction Check Point Research tracks a sustained, highly capable espionage cluster, which we refer to as Ink Dragon, and is referenced in other reports as CL-STA-0049, Earth Alux, or REF7707. This cluster is assessed by several vendors to be PRC-aligned. Since at least early 2023, Ink Dragon has repeatedly targeted government, telecom, and […]
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
You can email the...
Exploiting Anno 1404
### Summary
Clients are required in the [OAuth spec](https://datatracker.ietf.org/doc/html/rfc6749#section-10.12) to prevent CSRF attacks at its Callback handler. The implementation in [cloudflare...